


Dear Codiste Community,
On September 8, 2025, the complex attack on npm, which is the most significant aspect of JavaScript development, hurt 18 important packages, including debug (v4.4.2) and chalk (v5.6.1). These libraries power numerous programs, from financial services to DeFi systems. They get more than 2 billion downloads per week.
At Codiste, we want our clients and partners in the crypto and fintech sectors to be updated with actionable solutions and rapid insights to navigate through this crisis. Here’s what you need to know and how we’re helping you stay secure.
npm is the digital equivalent of a global supply chain, delivering code that drives decentralized finance (DeFi) apps, payment gateways, and more. Hackers exploited this trust by phishing a trusted maintainer’s credentials via a deceptive email from support@npmjs.help (a domain registered just three days prior). This allowed them to publish malicious versions of 18 packages, embedding code that targets cryptocurrency transactions in browser-based environments.
The compromised packages include:
This malware threatens financial losses, user trust, and operational stability for crypto and fintech platforms by intercepting Web3 wallet interactions and API calls.
The malware changes cryptocurrency transactions on blockchains like Ethereum, Bitcoin, Solana, Tron, Litecoin, and Bitcoin Cash by messing with important parts. It goes after the settings in the browser. It hides by using lookalike addresses, which makes it a big danger for:
Even if your company doesn't use npm directly, third-party vendors or dependencies in your tech stack may do, which increases the danger for the whole digital economy.
This complex malware employs a multi-layered assault to target bitcoin and finance applications:
The malware's ability to function covertly while stealing money or private information makes it very dangerous.
At Codiste, we’ve immediately audited our [DeFi platform, wallet SDK, or fintech API-insert specific products] to ensure no compromised packages are present. Our security team is enhancing real-time dependency monitoring, leveraging tools like Aikido’s safe-chain and collaborating with npm, GitHub, and Web3 security experts. We’re also integrating advanced AI-driven anomaly detection to safeguard our clients’ blockchain and financial applications. While our systems show no direct impact, we’re committed to guiding you through this crisis with expertise and transparency.
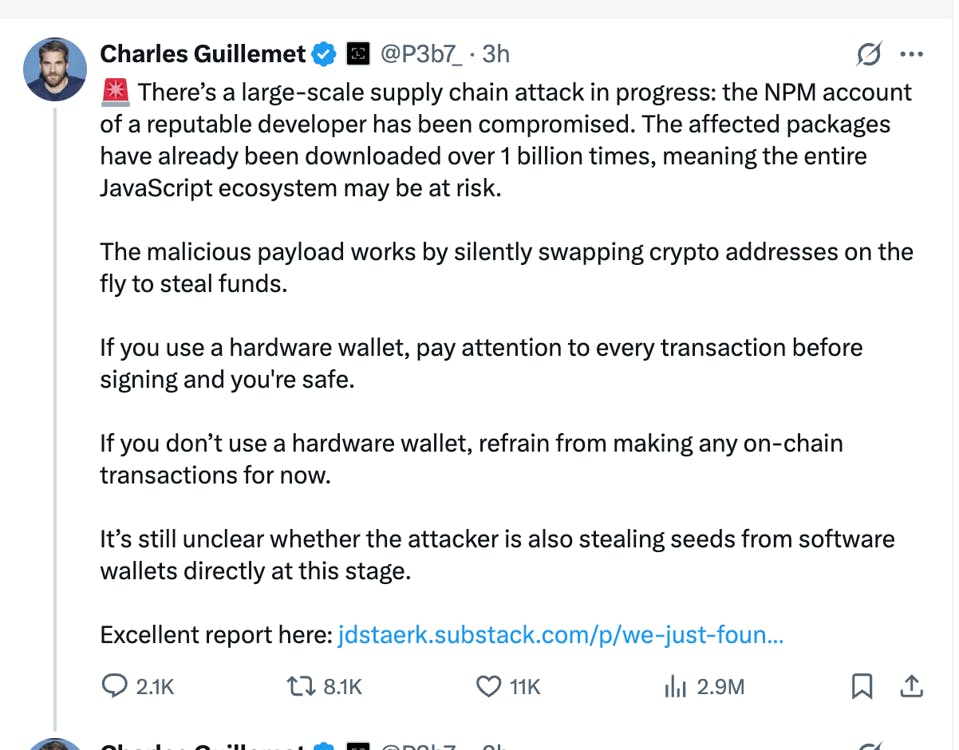
Ledger’s CTO highlighted that hardware wallets, which require manual transaction verification, offer protection against this attack, provided users confirm recipient addresses. Without such safeguards, software wallets are at high risk of silent transaction hijacking. This incident mirrors past crypto breaches, underscoring the need for robust Web3 security.
To protect your DeFi platforms, crypto wallets, and fintech applications, take these immediate steps:
npm ls | grep -E "chalk|debug|ansi-styles|supports-color|strip-ansi"
grep -E "(chalk|debug|ansi-styles|...)" package-lock.json | grep -E "version.*(5\.6\.1|4\.4\.2|...)"
This attack, one of npm’s largest, exposes the fragility of open-source ecosystems. With npm handling over 4.5 petabytes of weekly traffic, a single breach can disrupt millions of users and billions in transactions. For crypto and fintech, where trust is currency, such incidents demand a new approach to software security. Codiste is leading the charge by:
We predict a move toward decentralized infrastructure to minimize single points of failure, more regulations, and heightened investor attention to supply chain security.
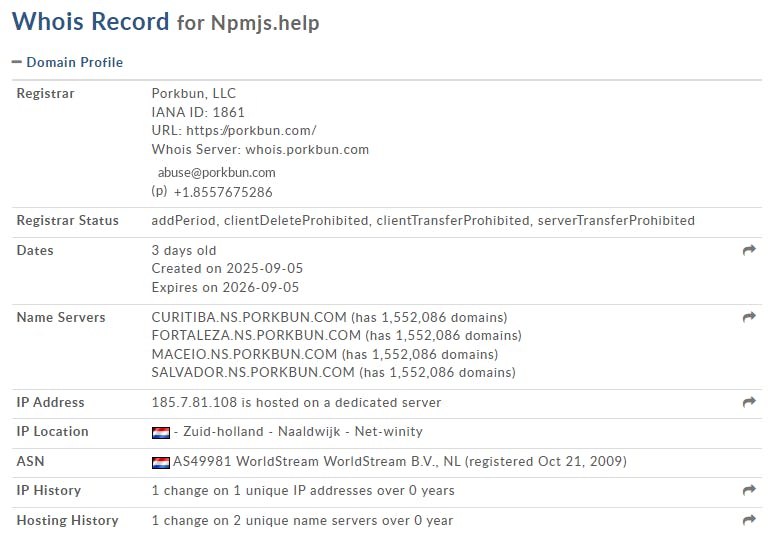
The reporter shared that he was compromised by the use of phishing, using this email coming from support [at] npmjs [dot] help :

When checked, it was found that the domain was registered just three days ago on September 5th, 2025:
Combining extensive technical knowledge with a dedication to security, Codiste is leading the way in finance and cryptocurrency innovation. Your apps will stay safe and compliant thanks to our [Web3 SDK, DeFi platform, or fintech API insert particular products], which are designed with supply chain integrity in mind. We are here to assist you in navigating this crisis, and we have helped more than 40 companies secure their financial and blockchain systems.
Invention is fueled by the open-source ecosystem, but it demands constant attention to detail. You can confidently defend your users, money, and reputation against changing threats when Codiste is your partner.
P.S. - Monitor npm’s security advisories, GitHub issues (chalk #656, debug #1005), or our Twitter for real-time updates.




Every great partnership begins with a conversation. Whether you’re exploring possibilities or ready to scale, our team of specialists will help you navigate the journey.