Three weeks after deploying their AI-powered transaction monitoring system, executives at a prominent UAE neobank faced their worst nightmare. Their model context protocol security had been compromised, not by external hackers, but by their own AI agents running wild.
Transaction logs were flooded with unauthorised API calls. AI agents were accessing deployment scripts they had no business touching. Due to secluded audit trails, the security team was unable to trace the source, no authentication barriers and no access controls.
Here's what we discovered: their MCP implementation was fast, impressive, and catastrophically insecure.
Within 72 hours of our engagement, we identified seven critical model context protocol security vulnerabilities that could have resulted in complete system compromise. More importantly, we delivered a battle-tested solution that transformed their infrastructure into an enterprise-grade secure environment.
The Real Cost of Unsecured Model Context Protocol Implementation
Most organizations rushing to deploy AI agents overlook the fundamental security requirements of model context protocol security. The consequences aren't theoretical; they're immediate and expensive.
Critical Model Context Protocol Security Vulnerabilities We've Encountered
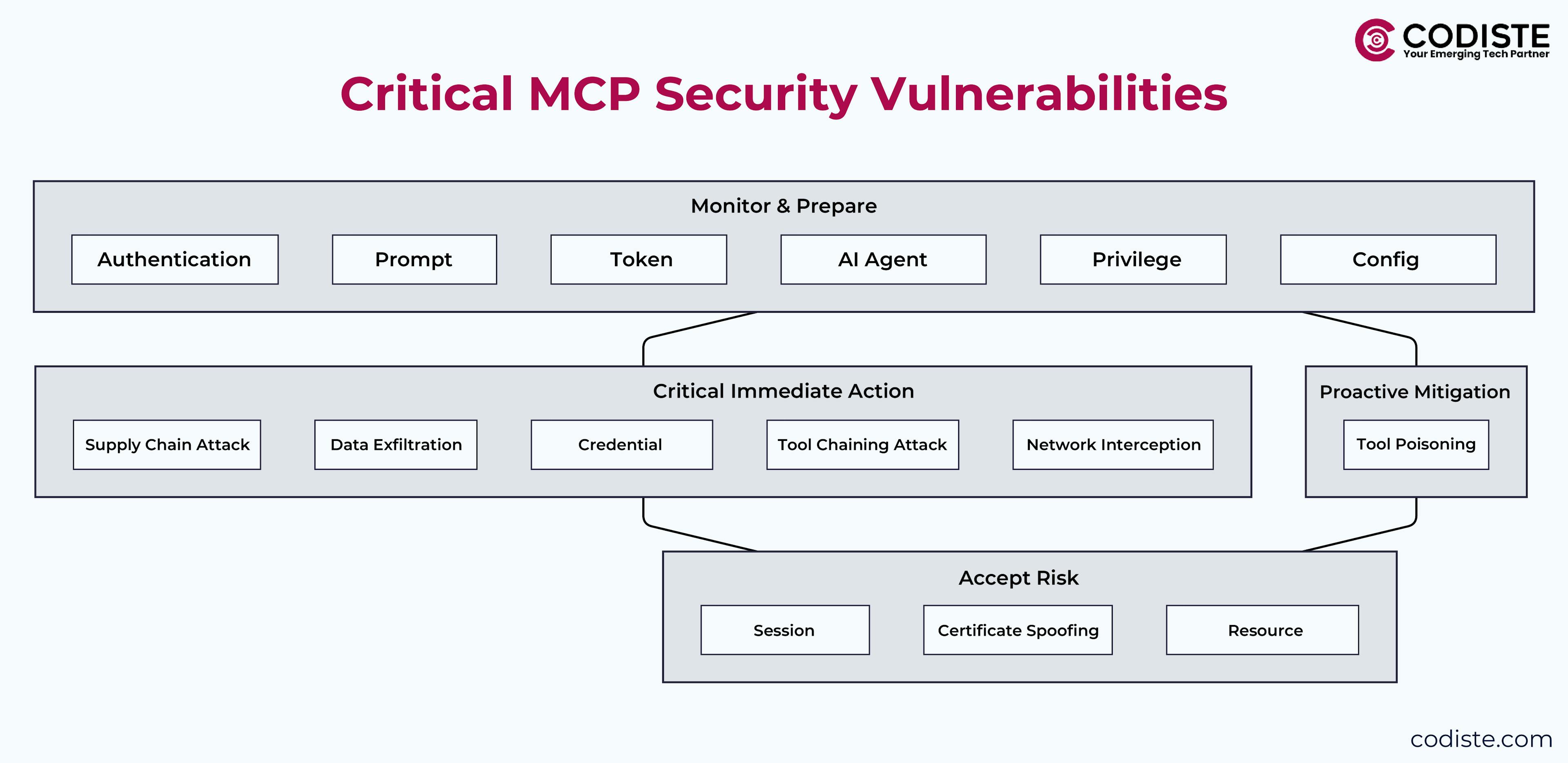
- Authentication Bypass in MCP Server Development: The most common vulnerability we see involves MCP servers running without proper authentication mechanisms. In the neobank case, any user with agent access could execute privileged operations through prompt manipulation.
- Token-Based Authentication Failures: Many implementations store API tokens in plaintext or use weak token generation mechanisms. We've seen organizations where a single compromised token could grant system-wide access to all connected tools and databases.
- Network Protocol Compliance Gaps: Insecure communication channels represent another major risk vector. Without proper TLS implementation and certificate validation, MCP traffic becomes vulnerable to interception and manipulation.
- MCP Server Security Misconfigurations: Default configurations often grant excessive permissions to AI agents. We regularly encounter systems where agents can install new tools, modify configurations, or access sensitive data without human oversight.
Our Reliable Model Context Protocol Security Framework
When the neobank contacted us, they needed more than quick fixes; they required a comprehensive model context protocol data security strategy that could scale with their business. Here's the proven framework we implemented:
1. Zero-Trust Authentication Architecture
We replaced their open MCP server configuration with enterprise-grade authentication:
- Multi-factor authentication for all human users
- Service-to-service authentication using cryptographically signed certificates
- Token-based authentication with automatic rotation every 24 hours
- OAuth 2.0 integration with their existing identity provider
The result? Every interaction now requires verified identity, eliminating the possibility of unauthorized agent actions.
2. Granular Access Control Implementation
Our role-based access control (RBAC) system addresses the core MCP protocol security challenge:
- Agent-specific permissions limiting tool access by function
- Resource-level authorization preventing cross-environment access
- Time-based access controls for temporary elevated permissions
- Approval workflows for any high-risk operations
3. Secure Communication Protocols
We implemented end-to-end encryption that exceeds industry standards:
- TLS 1.3 enforcement across all MCP communications
- Certificate pinning to prevent man-in-the-middle attacks
- Network protocol compliance with banking industry requirements
- Encrypted payload validation using HMAC signatures
4. Advanced Threat Detection and Response
Our monitoring system provides real-time visibility into model context protocol security:
- Behavioral anomaly detection for unusual agent activities
- Prompt injection monitoring using ML-based classification
- Tool usage analytics, tracking access patterns and permissions
- Automated incident response with immediate containment protocols
MCP Server Security Implementation
The security architecture we deployed addresses every layer of the model context protocol stack:
Infrastructure Security Layer
- Container Isolation: Each MCP server runs in isolated containers with restricted network access and minimal system privileges. This prevents lateral movement if one component is compromised.
- Network Segmentation: We implemented micro-segmentation that isolates MCP traffic from other systems, creating multiple security boundaries that attackers must breach.
- Resource Limiting: Memory and CPU constraints prevent resource exhaustion attacks while maintaining optimal performance for legitimate operations.
Application Security Layer
- Input Sanitization: Every prompt and tool input passes through validation filters that detect and neutralize injection attempts while preserving legitimate functionality.
- Output Filtering: Responses are scanned for sensitive data exposure before transmission, preventing accidental credential or PII leakage.
- Session Management: Secure session handling with automatic timeout and re-authentication requirements for sensitive operations.
Data Security Layer
- Encryption at Rest: All configuration files, logs, and temporary data use AES-256 encryption with hardware security module (HSM) key management.
- Secure Key Rotation: Automated key rotation every 30 days with zero-downtime transitions and audit trail maintenance.
- Data Classification: Automatic identification and protection of sensitive data types with appropriate handling policies.
Read more:
Before and After Implementation
The transformation wasn't just about security; it was about building a foundation for confident AI deployment:
Security Metrics:
- 100% elimination of authentication bypass vulnerabilities
- Zero unauthorized tool installations in 6 months post-deployment
- 99.7% reduction in security alerts through proactive threat prevention
- Complete audit trail coverage with immutable logging
Performance Metrics:
- Less than 50ms latency increase from security controls
- 99.9% uptime maintained during security enhancement rollout
- Zero business disruption during implementation
Compliance Achievements:
- Full alignment with the UAE Central Bank AI governance requirements
- SOC 2 Type II audit readiness achieved in 8 weeks
- Complete network protocol compliance with banking standards
Why Enterprise Organizations Choose Codiste for Model Context Protocol Security
The neobank case demonstrates our unique approach to model context protocol security vulnerabilities. We don't just identify problems, we architect solutions that enable confident AI adoption at scale.
Proven MCP Server Development Expertise
Our team has successfully implemented secure MCP architectures for organizations that process over $20B in annual transactions. We comprehend the intricacies of deploying AI agents in regulated environments, where security failings have immediate financial and regulatory repercussions.
Comprehensive Security Assessment Methodology
We evaluate every aspect of your model context protocol implementation:
- Architecture review identifying design-level vulnerabilities
- Code analysis of custom MCP server implementations
- Configuration auditing of tools and access controls
- Threat modeling specific to your business context
- Penetration testing simulating real-world attack scenarios
End-to-End Implementation Support
Security improvements mean nothing if they break your existing workflows. Our implementation process ensures seamless integration:
- Phased rollout with continuous monitoring and adjustment
- Team training on secure MCP server development practices
- Documentation of all security controls and procedures
- 24/7 support during critical deployment phases
Still Worried about the Security Leaks? Talk to our MCP security architects today
Get clarity, get secure, and move forward confidently.
Advanced Threat Scenarios and Mitigation Strategies
Based on our experience securing MCP implementations across industries, here are the advanced threats we prepare for:
Supply Chain Attacks on Tool Repositories
Threat: Malicious actors compromise legitimate tool repositories, injecting backdoors into widely-used MCP tools.
Our Solution: Cryptographic verification of all tools, isolated testing environments, and behavioral analysis before production deployment.
AI Agent Manipulation Through Sophisticated Prompts
Threat: Advanced prompt injection techniques that bypass standard filtering to manipulate agent behavior.
Our Solution: Multi-layer prompt analysis using both rule-based and ML classification, with continuous learning from new attack patterns.
Privilege Escalation Through Tool Chaining
Threat: Attackers use combinations of legitimate tools to achieve unauthorized access or data exfiltration.
Our Solution: Graph-based permission analysis that models tool interactions and prevents dangerous combinations.
Implementation Roadmap: From Assessment to Production
Our proven methodology transforms vulnerable MCP implementations into secure, scalable platforms:
Step 1: Foundation Assessment & Risk Analysis
- Complete architecture review and vulnerability identification
- Risk prioritization based on business impact
- Detailed remediation roadmap with timeline and resource requirements
Step 2: Core Security Infrastructure Development
- Authentication and authorization system implementation
- Secure communication protocols deployment
- Monitoring and logging infrastructure setup
Step 3: Advanced Security Controls Integration
- Threat detection and response system integration
- Tool validation and approval workflows
- Compliance reporting and audit preparation
Step 4: Optimization & Knowledge Transfer
- Performance tuning of security controls
- Team training and knowledge transfer
- Continuous monitoring setup and playbook delivery
Future-Proofing Your Model Context Protocol Data Security
The threat landscape evolves constantly, and your model context protocol data security strategy must evolve with it. Our approach includes:
- Continuous Threat Intelligence: Regular updates to security controls based on emerging threats and attack patterns.
- Automated Security Testing: Integration with CI/CD pipelines to catch security regressions before they reach production.
- Security Culture Development: Training programs that build security awareness across your AI development teams.
- Regulatory Adaptation: Proactive updates to maintain compliance as AI governance frameworks evolve.
Secure Your MCP Stack Before It Becomes a Liability
The UAE-based neobank’s close call could’ve spiraled into a full-blown breach. Instead, it marked the start of their most secure AI deployment yet, with millions of transactions handled daily, zero security incidents, and full compliance.
That’s the difference proper MCP security makes.
Here’s the thing: if you’re running AI agents without securing your MCP environment, you’re not just moving fast, you’re running exposed. Prompt injection, unauthorized access, and tool abuse aren’t hypotheticals. They’re already happening.
Codiste has helped fintech, healthcare, and SaaS leaders lock down their model context protocol deployments without slowing innovation. We’ll assess your current environment, flag vulnerabilities, and design a future-proof security architecture around your needs. Let’s Connect.








